
The Internet of Things (IoT) has revolutionized how we interact with technology, enabling smart devices to connect and communicate seamlessly. However, this convenience has come at a cost: an increase in cybersecurity vulnerabilities. Among the most significant threats are IoT botnets, networks of compromised devices exploited to execute large-scale cyberattacks. This article explores the evolving landscape of IoT botnets, focusing on the infamous Mirai botnet, and highlights proactive measures such as the UK’s Product Security and Telecommunications Act (PSTI) aimed at mitigating these risks.
What Are IoT Botnets?
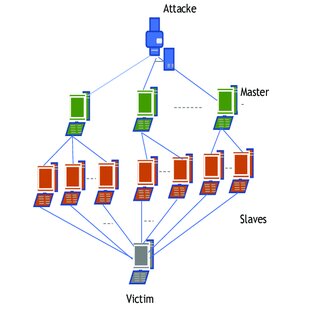
IoT botnets are networks of internet-connected devices, often compromised through malware, that are controlled remotely by malicious actors. These devices, ranging from CCTV cameras to smart refrigerators, are repurposed to perform coordinated cyberattacks like Distributed Denial of Service (DDoS), spam campaigns, and data breaches.
The concept of IoT botnets emerged as IoT devices proliferated across industries and homes. Despite their utility, these devices regularly lack robust security features, making them easy targets for attackers. Insecure configurations, such as default credentials and outdated firmware, further exacerbate the risk.
The Mirai Botnet Phenomenon
One of the most well-known IoT botnets, Mirai, was first identified in 2016. Its creators, Paras Jha and Josiah White, leveraged weak security practices in IoT devices, exploiting default usernames and passwords. Mirai’s most infamous attack targeted Dyn, a domain name system (DNS) provider, bringing down significant portions of the internet across the United States and Europe.
Despite the apprehension of Mirai’s creators, its source code was released online, leading to the development of several variants. These continue to pose significant risks, particularly as IoT device adoption grows.
How Mirai Exploits IoT Devices
Mirai’s modus operandi involves scanning the internet for devices running minimal Linux-based operating systems with ARC processors. The malware leverages default credentials to gain access, transforming the devices into “zombies” within a botnet. These compromised devices are then used for attacks, including DDoS campaigns and click fraud operations. The malware works in 4 phases as outlined below:
Infection Phase
- Scanning for Vulnerable Devices
Mirai uses a lightweight, aggressive scanning mechanism to identify IoT devices exposed to the internet. It primarily targets devices with default or weak credentials. These devices are often accessible via protocols like Telnet or SSH. - Credential Brute-forcing
The malware attempts to log in to the device using a hardcoded list of common username-password combinations. Once successful, Mirai injects its payload and takes control of the device.
Bot Enrolment
- Once infected, the device becomes part of the Mirai botnet. Communication between the infected devices and the Command-and-Control (C2) server is established to await further instructions.
Attack Phase
- Launching DDoS Attacks
The primary function of Mirai is to conduct Distributed Denial-of-Service (DDoS) attacks. It does so by flooding the target with massive amounts of traffic, overwhelming their infrastructure. Mirai supports multiple attack vectors, such as UDP flooding, TCP SYN flooding, and HTTP GET/POST request flooding, making it versatile against various target configurations.
Persistence and Clean-up
- Mirai deliberately limits its persistence by removing itself from the device’s storage. This prevents detection through traditional static analysis tools. However, it remains active in the device’s memory until reboot. Upon reboot, the device is no longer infected, but it may be re-infected due to continued exposure.
Why IoT Botnets Are a Growing Concern
Exponential Growth in IoT Devices
The global IoT ecosystem continues to expand, with billions of devices projected to be connected by 2030. As more devices enter the market, the attack surface for cybercriminals widens.
Lack of Security Standards
IoT manufacturers often prioritize functionality and cost over security. This results in devices with minimal protections, reused hardware, and software vulnerabilities that are ripe for exploitation.
Ease of Attack Execution
Botnet kits and malware-as-a-service platforms have made it easier for even low-skilled attackers to deploy sophisticated IoT botnets. This commodification of cybercrime exacerbates the threat.
The UK’s Proactive Measures: PSTI Act (Secure by Design)

In response to the growing IoT security crisis, the UK enacted the Product Security and Telecommunications Act (PSTI). This legislation aims to address key vulnerabilities in consumer IoT devices and enforce stricter security standards. Key mandates include:
- Unique Passwords: Devices must have unique, non-default passwords or allow users to set their own passwords upon setup.
- Security Issue Reporting: Manufacturers must provide clear guidance on reporting security vulnerabilities.
- Security Updates: Manufacturers must disclose the minimum period during which devices will receive security updates.
Why the PSTI Act Matters
Addressing Default Password Risks
Default passwords are a primary entry point for IoT botnet malware like Mirai. By mandating unique passwords, the PSTI reduces the likelihood of mass exploitation.
Consumer Awareness and Action
The requirement for security issue reporting and update transparency empowers consumers to make informed decisions and maintain device security over time.
Mitigation Strategies for IoT Botnets
Network-Level Security
Implementing network-level protections such as firewalls, intrusion detection systems, and traffic filtering can help mitigate botnet activity.
Consumer Best Practices
Consumers should:
- Regularly update IoT device firmware.
- Change default passwords to strong, unique ones.
- Disable unnecessary features and services on devices.
Industry Collaboration
Manufacturers, regulators, and cybersecurity experts must work together to establish global IoT security standards and enforce compliance.
Future Prospects for IoT Security
Expanding Legislation
The PSTI Act is expected to incorporate additional principles from the ETSI EN 303 645 standard, such as secure communication and simplified device maintenance. These measures will further strengthen IoT security frameworks.
Emerging Technologies
Artificial intelligence (AI) and machine learning (ML) are being leveraged to identify and neutralize botnet threats in real time. Innovations like post-quantum cryptography also promise to enhance device security.